Internal Control in an Electronic Data Processing system
Internal controls in computer based accounting system are of two basic types:
1) General controls or organization controls
2) Application or procedural controls
Internal control in a computer based accounting system can be represented by the following diagram.
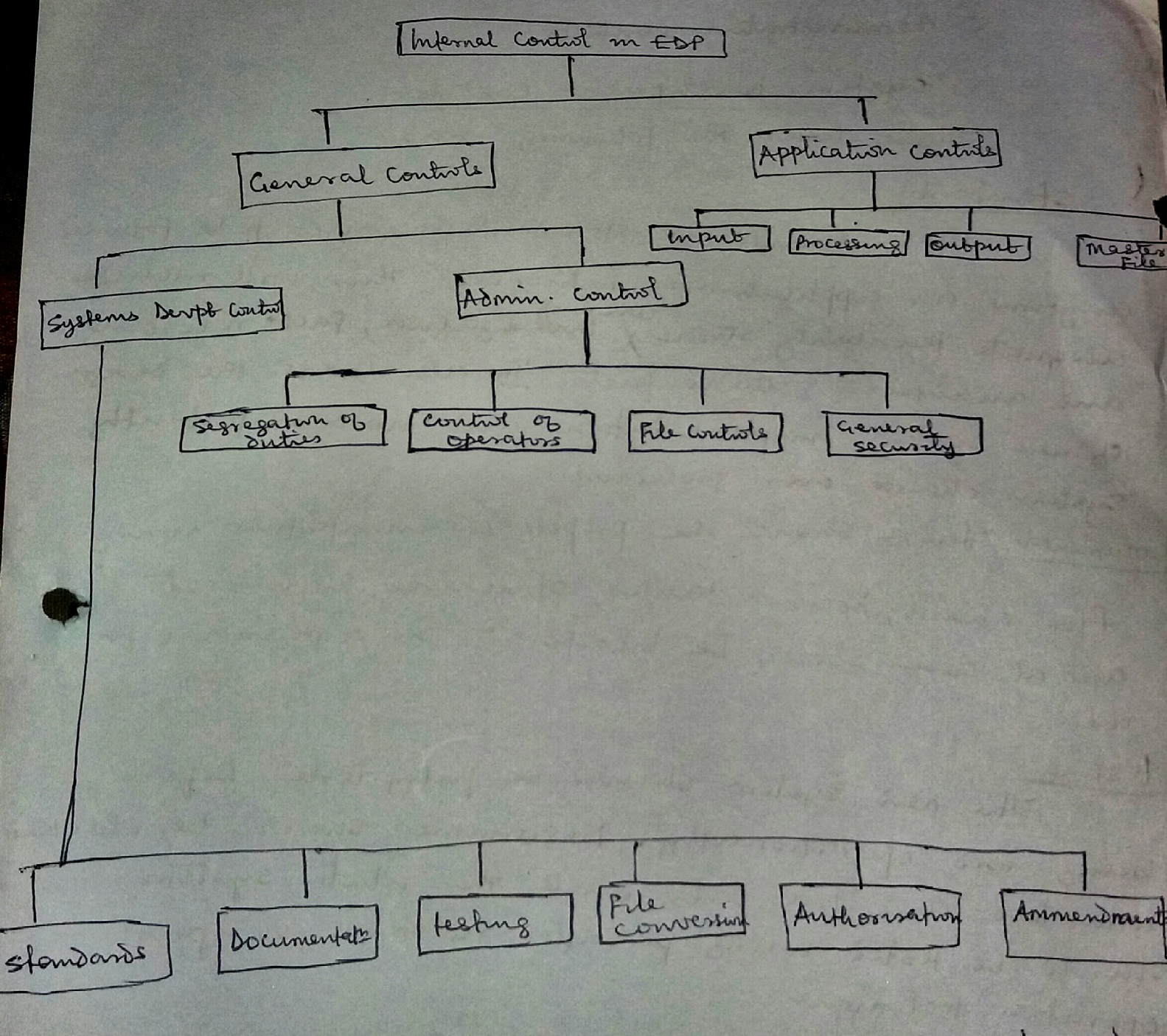
General controls
This control covers the environment in which computer processing is conducted. Some of the objectives of general control include:
a) To ensure adequate segregation of duties, that is, division of functional responsibilities
b) To protect information contained in computer records etc. General controls can be subdivided into:
i) Systems development and control
ii) Administrative controls
Systems development and control
This covers the following areas:
Standards: There should be standard procedures to be followed anytime an application is introduced. This will include adequate feasibility studies covering investigation, fact recording and analysis of gathered facts. It also covers the design of new systems, implementation and most importantly systems change over procedure.
Documentation: There should be proper documentation using flow charts, decision tables, structured English etc and all these should be incorporated in a manual for use.
Testing: The new system should be fully tested before being used operationally. Programs should be checked with test and live data while the whole system should be tested using parallel running or pilot operation technique.
File conversion: Before the new system becomes operational, master files should be set up completely and accurately. This can be achieved by a complete print out of the contents of master files and crosschecking the results with manually maintained records. This process is referred to as conversion checks.
Authorization: Each system development stage should be reviewed by a responsible officer in the EDP department and it must be approved by the steering committee or board of directors but most importantly, it must be acceptable to user department.
Amendment
Changes to operational system or programs should be subjected to the same controls as initial development. It must be authorized and controlled.
Conclusion.
It is important to consult with auditors because they would want to ensure that sufficient control is present in the new system to maintain reliable accounting records.
Administrative Controls
This includes:
a) Division or segregation of duties: Data processing staff should not initiate transactions or authorize normal transactions while users should not operate the computer by self to process transactions. In modern system, this division is not practicable since some authorization function is implicitly transferred to computers. For example, a computer raising purchase requisition when stock reaches re-order levels. Also, the main functions within the data processing department should be carried out by separate persons. Only user department staff and data processing department staff should be allowed to amend input data while computer operators should have access to the machines during a processing run.
However, small companies may be constrained by inadequate human and financial resources which must be balanced with increased supervision by responsible officers.
b) Control over computer operators.
There should be control over computer operators using manual with details of standard procedures to be followed always. There should be frequent and independent review of computer usage by references to clerical and machine logs.
There should be rotation of operators’ duty and a minimum of two operators per shift.
c) File control
This will cover:
i) File storage procedure: This involves the use of locks and keys on computer files and programs. These devices should be kept in a conducive atmospheric environment. A record of file usage should be maintained and ensure its prompt returns.
ii) File identification procedures: Which includes physical label by allocating unique identification no to the file which can be manually checked.
iii) Protection rings or written permit rings for magnetic tapes or disc files must be physically attached before any processing. Machine labels using header and trailer labels such as file name, identification number, retention period will be checked by a computer programmer on set up.
iv) File reconstruction procedures: This involves recreation when contents of computer files are lost, stolen or damaged. This can be achieved by retention of earlier generation of master file and related transaction data’s file such as Grand father, father son technique for magnetic tapes, dumping or copying for magnetic disc or diskette.
d) General security: There should be restriction of access to computer facilities by beating the equipment in a room with locks. Camera facilities may also be employed.
Standby arrangements such as power generating plants supplemented by uninterrupted power supply (UPS) should be provided for. Maintenance agreement should be signed with the computer vendor. Adequate insurance policy should be obtained to cover risk of fire, flood etc.
Application or procedural control:
This includes:
Input, processing, output and master file controls. These controls are to ensure the completeness and accurate processing of data.
a) Input controls: There should be segregation of duties between users and EDP functionals. For example, input should be originated by users only, and amendments should be done by authorized personnel.
There should be segregation of duties between punching and verification when converting input into machine sensible form. There should be physical control over source documents (such as vouchers, sales invoices) input media (such as magnetic tapes, disc and diskettes). There should be procedures for recording investigating errors and resubmission for processing. Batch control (such as control total, batch total and hash or nonsense total) to be used in order to achieve completeness and accurate processing. Control total involves counting the number of documents in a batch for control purposes .If this count is found to be incorrect at a later stage in the system, the batch can then be checked to find out what has gone wrong.
Batch total involves choosing a quantitative field and accumulating its value together for control purposes. Examples of quantitative fields are : total values of invoices, total value of overtime payments, total quantity sold etc. Harsh total involves choosing a field which has no quantitative meaning and accumulating its value together. Examples are: totals of invoice members, customer numbers, pay-roll numbers etc the total of which are meaningless but useful for control purpose; thus, the term or name harsh or nonsense total.
Also, validation checks or data vet or edit control can be built or programmed into input conversion to validate input for reasonableness. Examples are types or data vet or field or character check, limit or range check, existence check, reasonableness check, sequence check, completeness check.
Processing control
This relates to all arithmetic and logic operations or input carried out by programmed procedures such as edit controls or data vet.
Check digit verification
A check digit is a number which is added to a series of reference numbers for the purpose of producing a self checking number. Each check digit is derived mathematically and bears a unique mathematical relationship to the number to which it is attached. When the reference number is input into the system, the validation programme performs the same calculation and the resultant remainder should be zero. If not then the reference number is incorrect. The objective of the check digit verification is to prevent transposition and transcription errors.
Field|Characteristics|type|format|presence check
Under this, data is checked to ensure that all necessary fields are present and that the fields contain the correct type of characteristics; that is there are no letters in a numeric field.
Limit or range check
Numbers are checked to ensure that they are within the permissible range or limit and any data outside these limits will be rejected.
Completeness check
This includes control, batch and nonsense totals.
Sequence check
This is to check sequence failure and duplicate records
Screen check
This involves operators’ scrutiny before the data is processed by the computers. It also involves pre-formatting of screen to minimize operator error.
Existence check
This involves testing reference numbers with previously established list of valid numbers held on a computer file or in the programme in order to ensure that only valid general ledger codes are input.
Reasonableness check
This is to check whether the data is reasonable in relation to a standard or previous input. Examples are hours worked, interest rate, units of utility consumed and prices of goods received.
Output control
There should be reconciliation or matching of input totals established prior to processing to computer generated output totals. There should be manual checking through on a sample basis of the basic calculations carried out by the computer such as depreciation charges, direct debit etc. There should be a procedure for distributing output, that is, a list of authorized recipients should be maintained. An output register should be used to monitor distribution and confirm receipts. These should be independent review of exception reports.
Master file controls
There should be proper control over input, processing and output amendment. That is, once written; standing data or stable data should remain unaltered until an authorized change is made. There should be periodic print out of standing data (such as customer’s name & address, standard and overtime rates, employee name and location etc) For checking with manually held information. There should be regular print out of individual balances such as debtors, creditors etc for comparison with customer statement of account.
Recommended Reading
O. Ray Whitting.,Wiley CPAexcel Exam Review: Auditing and Attesting






Leave a Reply